What Is Kubernetes?
Kubernetes is an open-source platform designed to automate deploying, scaling, and operating application containers. It groups containers that make up an application into logical units for easy management and discovery. Originating from Google, Kubernetes has become ubiquitous in container orchestration, enabling organizations to manage their containerized applications more efficiently across various environments.
Kubernetes can manage clusters of hosts running Linux containers. It simplifies rolling updates, system monitoring, and scaling by allowing users to declare their infrastructure in code rather than manually setting up individual servers. This declarative approach ensures applications run as intended across different environments, making deployments more predictable and scalable.
The Importance of Handling Kubernetes Errors
Proper handling of Kubernetes errors is crucial for maintaining the reliability and efficiency of applications deployed on the platform. Errors can disrupt service operations, leading to downtime and negatively impacting user experience. By identifying and addressing errors promptly, teams can ensure their applications remain available and performant, minimizing potential disruptions to their services.
Understanding the nature of these errors and implementing strategies for their resolution helps in optimizing application performance in Kubernetes environments. This involves troubleshooting when issues arise and proactively monitoring for potential problems in configuration and deployment to prevent common errors from occurring.
Common Errors You’ll Encounter in Kubernetes Environments and How to Fix Them
Here are some of the most common errors that arise in Kubernetes.
ImagePullBackOff
The ImagePullBackOff error occurs when the container runtime fails to pull a container image from a registry. This can happen for several reasons, such as incorrect image names, authentication failures with the image registry, or network issues.
To diagnose and resolve this error, you can first use the kubectl describe pod <pod-name> command to get more details about the error. This command provides specific information about why the image pull failed.
For example, if the issue is due to an incorrect image name, you might see an output like this:
Failed to pull image "myregistry/myimage:tag": rpc error: code = Unknown desc = Error response from daemon: manifest for myregistry/myimage:tag not found
To fix this issue, ensure that the image name and tag specified in your deployment configuration are correct and that the image exists in the registry. If the problem is related to authentication, you’ll need to create a secret in Kubernetes that contains your registry credentials and reference it in your deployment configuration. For network-related issues, verify that your Kubernetes nodes have proper Internet access and can reach the image registry.
CrashLoopBackOff
A CrashLoopBackOff error signals that a container is repeatedly crashing after being restarted by Kubernetes. This typically results from application errors, misconfigurations, or dependency issues within the container.
To troubleshoot, use kubectl logs <pod-name> to examine the logs of the failing container. These logs often provide insights into why the container is not starting properly. For example, if an application crashes due to a missing environment variable, the logs might contain an error message like:
Error: Missing required configuration ENV_VARProcess exited with status 1
To resolve this issue, ensure all necessary environment variables are defined in your deployment manifest. If dependencies are causing the crash, verify that all required resources are available and correctly configured before the application starts.
FailedScheduling
The FailedScheduling error occurs when Kubernetes is unable to assign a pod to any node. This can be due to insufficient resources, taints that prevent the scheduling, or affinity/anti-affinity rules that cannot be satisfied.
To diagnose, run kubectl describe pod <pod-name>, which may reveal why the pod cannot be scheduled. For example:
Events: Type Reason Age From Message
------- ------ ---- ---- ------- Warning FailedScheduling 30s (x24 over 3m) default-scheduler 0/3 nodes are available: 3 Insufficient cpu.
This output indicates a lack of CPU resources available on all nodes. To fix this, you might need to adjust the resource requests in your pod specifications based on the capacity of your existing nodes or add more nodes with sufficient CPU resources. If taints or affinity rules are the cause, review and adjust them in your deployment configuration to ensure pods can be scheduled successfully.
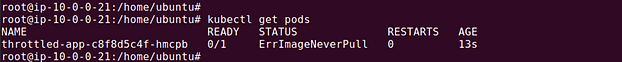
ErrImageNeverPull
The ErrImageNeverPull error in Kubernetes indicates that the container image is set not to be pulled from the registry, regardless of its presence or absence on the node. This scenario typically occurs when the imagePullPolicy is explicitly set to Never in the pod’s configuration. For example:
spec:
containers:
- name: mycontainer
image: myregistry/myimage:tag
imagePullPolicy: Never
To resolve this issue, you need to either change the imagePullPolicy to Always or IfNotPresent, ensuring Kubernetes attempts to pull the container image from the registry if it’s not available locally on the node.
Alternatively, if using local images for development purposes, ensure the required image is preloaded on all nodes where pods might be scheduled:
spec: containers:
- name: mycontainer
image: myregistry/myimage:tag
ImagePullPolicy: IfNotPresent
ConfigMap and Secrets Misconfiguration
ConfigMap and Secrets misconfiguration in Kubernetes can lead to application failures or, worse, security vulnerabilities. ConfigMaps are used to store non-confidential data in key-value pairs, while Secrets are intended for sensitive information. An example of a common misconfiguration is exposing sensitive data through a ConfigMap instead of a Secret:
apiVersion: v1
kind: Config
Mapmetadata:
name: app-config
data: username: user
password: pass
To correct this, sensitive data should be stored as Secrets and referenced securely within the application. Here’s how you can define a Secret and reference it:
apiVersion: v1
kind: Secret
metadata: name: app-secret
type: Opaque
data:
username: dXNlcg==
password: cGFzcw==
---
apiVersion: v1
kind: Pod
metadata: name: mypod
spec:
containers:
- name: mycontainer
image: myimage
envFrom: - secretRef:
name: app-secret
In this configuration, the username and password are base64 encoded (as required by Kubernetes Secrets), ensuring that they’re not stored as plain text. By referencing app-secret in the pod specification, the application can securely access these values without exposing them to unauthorized users or applications.
Conclusion
Understanding and resolving common errors is a key part of maintaining an efficient deployment environment in Kubernetes. This article has described several prevalent issues, such as ImagePullBackOff, CrashLoopBackOff, and misconfigurations with ConfigMaps and Secrets, offering practical solutions to address these challenges.
By leveraging these insights, developers and administrators can enhance their Kubernetes proficiency, ensuring applications are deployed seamlessly and operate reliably within the platform. Understanding Kubernetes errors is an ongoing process of learning and adaptation. As Kubernetes continues to evolve, so too will the strategies for troubleshooting and optimizing deployments.
Author Bio: Gilad David Maayan
Gilad David Maayan is a technology writer who has worked with over 150 technology companies including SAP, Imperva, Samsung NEXT, NetApp and Check Point, producing technical and thought leadership content that elucidates technical solutions for developers and IT leadership. Today he heads Agile SEO, the leading marketing agency in the technology industry.